Security
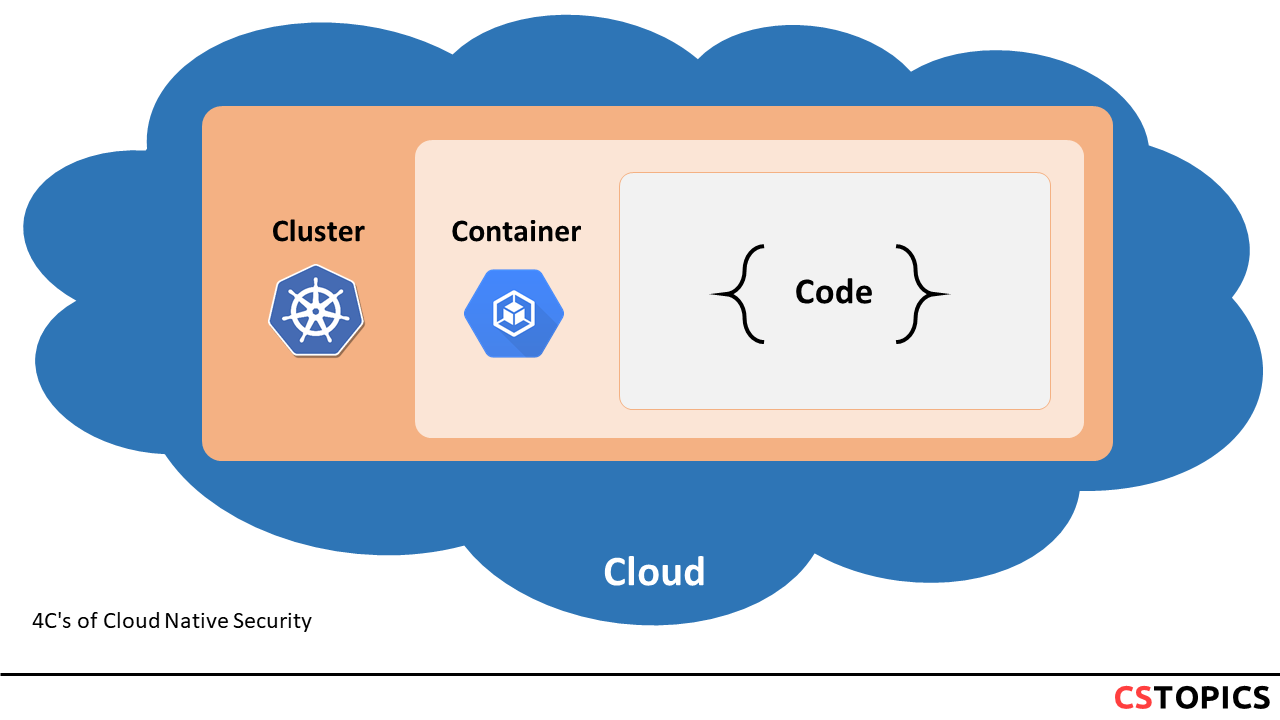
4C's of Cloud Native Security
Cloud native security refers to the set of practices and tools used to secure applications running in cloud environments.
The 4C's of cloud native security are: * cloud * clusters * container * code
Each of the 4C's plays a critical role in securing cloud native applications.
Cloud Security
- Cloud security involves securing the infrastructure and services used to host cloud native applications.
- Cloud security includes network security, identity and access management, and data security.
- Cloud security measures include firewalls, intrusion detection and prevention systems, and encryption.
Cluster Security
- Cluster security involves securing the nodes and services that make up a Kubernetes cluster.
- Cluster security includes node security, network security, and access control.
- Cluster security measures include role-based access control, network policies, and secure node configuration.
Container Security
- Container security involves securing the containers that make up a cloud native application.
- Container security includes container image scanning, runtime security, and access control.
- Container security measures include container image vulnerability scanning, runtime monitoring, and container network policies.
Code Security
- Code security involves securing the code that makes up a cloud native application.
- Code security includes code review, vulnerability scanning, and access control.
- Code security measures include code review processes, vulnerability scanning tools, and secure code signing and deployment processes.
Cloud Security Best Practices
Image: [Insert an appropriate image related to cloud security best practices]
Bullet points:
Cloud security best practices include using multi-factor authentication, implementing network segmentation, and encrypting data at rest and in transit. Other cloud security best practices include monitoring for security events, implementing security policies and procedures, and regularly patching and updating systems. Slide 7: Cluster Security Best Practices
Title: Cluster Security Best Practices
Image: [Insert an appropriate image related to cluster security best practices]
Bullet points:
Cluster security best practices include using role-based access control, implementing network policies, and using secure node configurations. Other cluster security best practices include monitoring for security events, implementing security policies and procedures, and regularly updating and patching Kubernetes. Slide 8: Container Security Best Practices
Title: Container Security Best Practices
Image: [Insert an appropriate image related to container security best practices]
Bullet points:
Container security best practices include scanning container images for vulnerabilities, implementing runtime security measures, and using container network policies. Other container security best practices include using secure container configurations, monitoring for security events, and implementing security policies and procedures. Slide 9: Code Security Best Practices
Title: Code Security Best Practices
Image: [Insert an appropriate image related to code security best practices]
Bullet points:
Code security best practices include using code review processes, scanning code for vulnerabilities, and using secure code signing and deployment processes. Other code security best practices include monitoring for security events, implementing security policies and procedures, and regularly updating and patching software.